Vulnerability Management
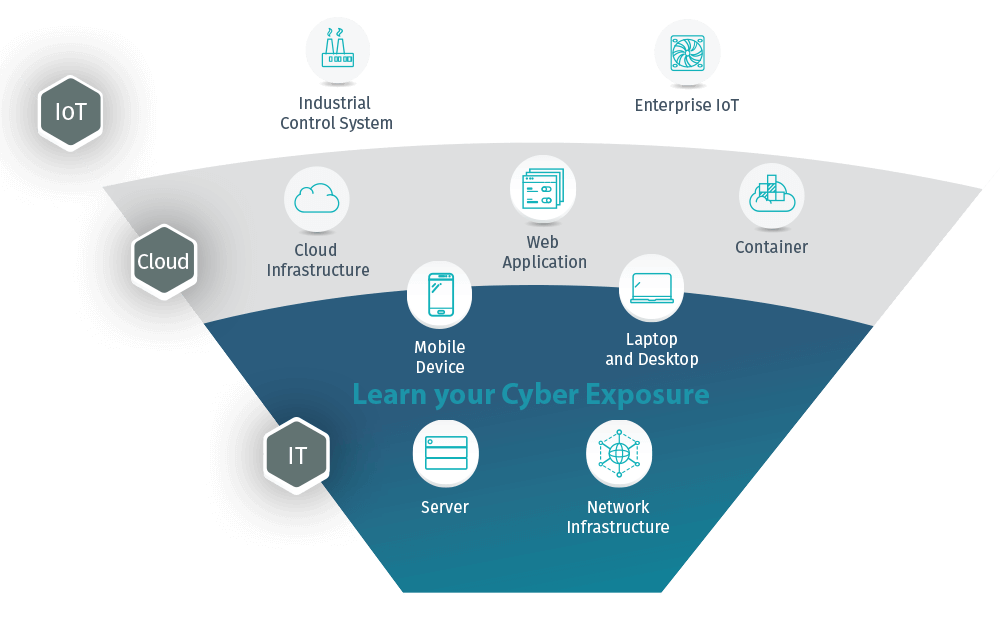
Organizations of all sizes have embraced digital and cloud transformation for efficiency and cost. Remote working, personal devices, cloud, SaaS have compounded the threat to IT teams to keep data secure. Access from anywhere is not part of our mutual future. But with the convenience, there are much higher risks. The truth is, there are not enough IT analysts to even defend networks. The after-hours attacks will relentlessly probe networks to find their weak points and will work their way into a network. There are now 10 billion IoT devices deployed in the enterprise and over 90% of organizations have applications running in the cloud today. Manage your vulnerability by having BorderLAN deploy Tenable, a leading global tool to know what to focus on.
Our Customers no matter how large or small can answer five questions at all times:
![]() Where are we exposed?
Where are we exposed?
![]() What should we Patch to avoid vulnerability
What should we Patch to avoid vulnerability
![]() Where should we prioritize based on risk?
Where should we prioritize based on risk?
![]() Are we reducing our exposure over time?
Are we reducing our exposure over time?
![]() How do we compare to our peers?
How do we compare to our peers?
Case Study
Sentara Healthcare
Vulnerability Prioritization: The key to security when lives are on the line
Sentara isn’t just Virginia’s largest
Being able to prioritize what we work on in terms of vulnerabilities and threats is crucial. There’s this constant churn of awareness and stress over deciding ‘well, what do we patch first?’




